A messaging system, by necessity, uses transactional behavior internally. It may be useful for an external client to be able to control the scope of the transactions that impact its behavior.
How can a client control its transactions with the messaging system?
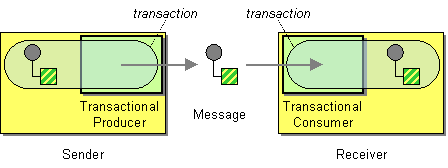
Use a Transactional Client—make the client’s session with the messaging system transactional so that the client can specify transaction boundaries.
Both a sender and a receiver can be transactional. With a sender, the message isn’t “really” added to the channel until the sender commits the transaction. With a receiver, the message isn’t “really” removed from the channel until the receiver commits the transaction. A sender that uses explicit transactions can be used with a receiver that uses implicit transactions, and vise versa. A single channel might have a combination of implicitly and explicitly transactional senders; it could also have a combination of receivers.
... Read the entire pattern in the book Enterprise Integration Patterns
Example: (Not quite) Transactional Client in Amazon SQSNEW
Transactional Client semantics can cause serious performance degradation in widely distributed systems. Many cloud-based messaging systems therefore don't implement Transactional Clients. However, these systems still aim to provide protection against client s crashing after they consume but before they process a message. The Amazon Simple Queuing Service (SQS) provides this protection via so-called Visibility Timeout. In this configuration, message consumers don't actually remove messages from the queue - the message simply becomes invisible to other consumers. After successfully processing the message, a message consumer must explicitly delete the message from the queue. If a message is not deleted, it becomes visible again to other consumers after the set timeout interval expires.
The book Cloud Computing Patterns documents this behavior as a distinct pattern called Time-out Based Delivery.
Related patterns:
Channel Adapter, Competing Consumers, Document Message, Event-Driven Consumer, Event Message, Guaranteed Delivery, Message, Message Channel, Message Dispatcher, Message Endpoint, Message Router, Message Sequence, Message Translator, Messaging Bridge, Pipes and Filters, Point-to-Point Channel, Polling Consumer, Publish-Subscribe Channel, Request-Reply, Resequencer






